H4xx0r3d! – how I found out that I am running a spam blog
Wednesday, March 3rd, 2010Yesterday, actually ten minutes before I had to leave for Kilburn to give my talk at ignite I had a shocking moment. I found in one of the sub-folders of my vast server a blog that offers cheap OEM software:

All of these links sooner or later redirect to firemicrosoft.net which is owned by someone in Russia and hosted by GoDaddy.
Don’t make folders writable to the world
What happened is that I had a very old guestbook script I had written once still running in this folder. The trick back then (and advocated by a lot of PHP tutorials as it is much easier that way) was to chmod a folder to 777 (read/write/execute permission for all) to store flat files in it. That was good enough for me back then (around 2000) and guess what? It was good enough for the spammers to store their blog.
Static page generation – in bulk
The blog was set up quite craftily in terms of SEO: Search Engines love static pages, so instead of accessing a DB - which wasn’t compromised – they simply created static pages for all the search queries that came in. After all this is about showing links and Google juice, not about delivering content. In the end, I found that I had 23487 HTML files advertising spam. Thank god for SSH access as this would have taken some time to delete over SFTP.
I investigated last night and I am happy to say that this is all that happened. If I found a folder to store whatever I pleased into I’d have also tried to read other files, including the wp_config.php for example.
Google Reader as a whistle blower
The interesting part about this is how I came to find out about it: Google Reader. I have a Google blog search RSS feed in my reader that notifies me every time someone links to http://wait-till-i.com – I found this much more useful than trackbacks which seem only to be used by spammers these days anyways:
In this feed I got a lot of posts from http://vancouverisawesome.com/:
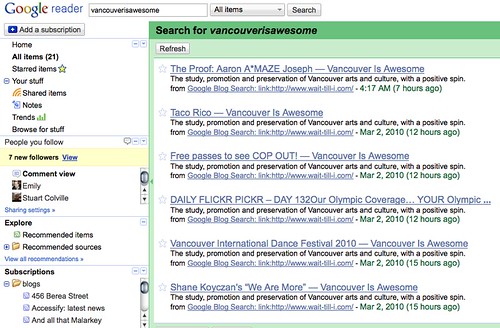
I thought at first that this is because of http://winterolympicmedals.com – after all it is timely for that. When I looked at the source code of this site, however, I found that just before the closing BODY tag spammers had injected links to different sites advertising OEM software:
width:100%; height:20px; z-index:1; visibility: hidden”>
[... lots of links interspersed with random HTML …]
At first I sniggered about them linking to a folder on my site I know that doesn’t exist but when I clicked the link and found the blog my smile vanished quickly.
See the whole stuff on pastebin – as you can see, all in all eight sites were attacked the same way.
What I find curious is that the links on vancouverisawesome are hidden and seem to still be indexed by Google – I remember being almost kicked out of AdSense once for absolutely positioning ads. Also, the links might be on the top of the screen but in the document are way down the tree, and vancouverisawesome is quite packed with links already.
I’ve cleaned up my server and I have contacted the maintainers of the other seven sites (and got a lot of “thank you” for that). I also contacted vancouverisawesome about them having spam links in the bottom. This is a pretty common attack (we had it on Ajaxian.com, too) targeted at WordPress installs.
How to avoid all this (and how to detect it)
So in order to make sure that this doesn’t happen to you:
- Do not leave folders writable to the world – if a piece of software tells you that you need to do this tell them to change it – it is inviting spammers like a dog turd invites flies.
- Do monitor your incoming links – if I hadn’t had the blog search RSS feed running I probably wouldn’t have found the blog until it really showed up in my traffic stats.
- Always upgrade your WordPress install – this is automated now and takes a second – there is no excuse not to.
- Redirect or – in the most extreme case – delete old things on your server that you don’t maintain any longer.